Security
Advancing the checkpoint environment
The Transportation Security Administration (TSA) continues to experience record breaking travel volume, and as passenger loads continue to grow, TSA continuously seeks to improve security. Here, Austin Gould, TSA’s Assistant Administrator for Requirements and Capabilities Analysis, discusses how the organisation is looking for innovative ways to address the evolving transportation challenges of today – and prepare for the challenges of tomorrow.
WITH THE threat to aviation constantly evolving, TSA is focused on developing the next generation of state-of-the-art security technology, which will be used to revolutionise the way airports operate.
Computed Tomography (CT)
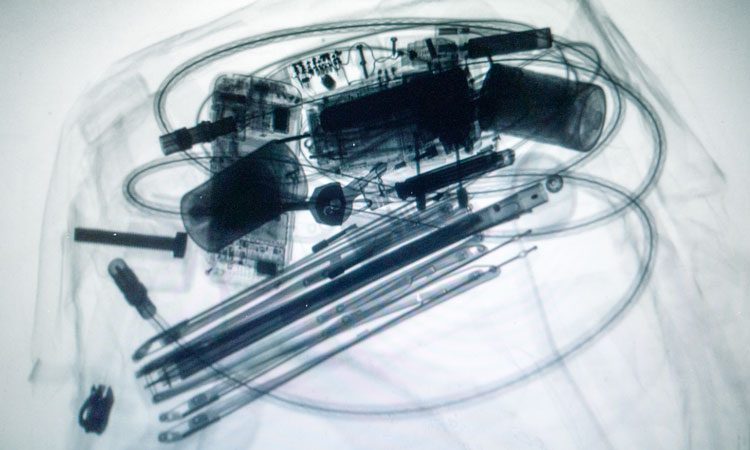
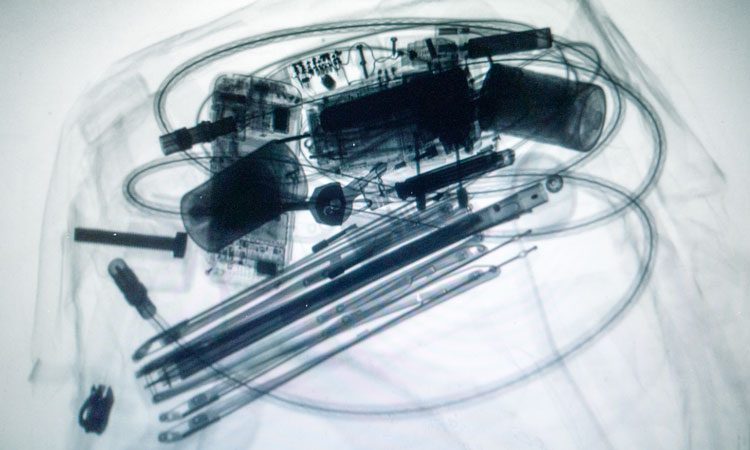
CT is the latest checkpoint X-ray scanning equipment to enhance threat detection capabilities for carry-on baggage. The technology is similar to CT technology used in the medical field and research shows that CT is the most consequential technology available today for airport checkpoints. CT technology applies sophisticated algorithms for the detection of explosives and other threats by creating a 3D image that can be viewed and rotated 360 degrees for a thorough analysis. If a bag requires further screening, TSA officers will inspect it to ensure there are no prohibited items inside.
Biometrics
With the rising use of biometrics for identity verification, TSA is evaluating the operational and security impacts of using passengers’ biometrics to verify their identities. Using biometrics will modernise aviation passenger identity verification over the coming years. TSA is actively evaluating facial recognition technology to automate the identity and boarding pass verification process. Facial recognition technology is currently being piloted at Hartsfield-Jackson Atlanta International Airport in conjunction with U.S. Customs and Border Protection.
Automated screening lanes (ASLs)
ASLs enhance security efficiency while decreasing the amount of time travellers spend during the security screening process. The ASLs are designed to improve the screening of passengers by automating many of the functions that were previously performed manually. The advanced screening system allows passengers to move faster and more efficiently through the security checkpoints. The automated conveyor belts draw bins into the X-ray machines and return the bins back to the front of the queue for passengers. Radio Frequency Identification (RFID) tags attached to each bin allow for additional accountability of a passenger’s items as they transit throughout the security process. Cameras capture photographic images of the contents of each bin, which are linked side-by-side to the X-ray image of a bag’s contents. Carry-on bags that trigger an alarm warning of a potential threat are automatically redirected to a separate area to allow bins behind them to continue through the screening process uninterrupted.
Enhanced advanced imaging technology (eAIT)
eAIT is a millimetre wave checkpoint passenger screening technology with enhanced detection capabilities that improve security and may help ease passenger experience. The AIT system has several benefits, but most noticeable to passengers is the relaxed stance, which means that instead of holding their arms over their heads, they can keep them down and close to their sides. The actual scan takes less than a second, and the addition of two screening stations allows those who need additional screening to move to a separate area until they are cleared by a TSA officer.
Credential authentication technology (CAT)
CAT units scan a passenger’s photo identification to verify the authenticity of the document. The system uses information from the photo identification to confirm a passenger’s flight status by cross-referencing it against the Secure Flight database. CAT enhances security by effectively verifying passenger identification to determine whether the documents presented at the checkpoint are authentic, fraudulent or expired, verifying the passenger’s Secure Flight vetting status in near real time. When CAT is in use, the TSA officer will not request the passenger’s boarding pass unless the system is not able to access the individual’s boarding information.
Innovation Task Force (ITF)
As TSA continues to raise the baseline for aviation security, we look to organisations who will help to advance capabilities, introduce new ways of thinking and bring creative solutions to travel challenges. TSA’s ITF was created to bring together key stakeholders to identify and demonstrate emerging technology solutions. ITF demonstrations allow vendors to test their solutions in a live environment, capture operational data and then refine their solution for potential future engagement with TSA.
Advancing the checkpoint environment (ACE)
ACE is a new, live checkpoint environment at LAS that serves as a ‘green space’ to assess multiple process and technology enhancements to the checkpoint environment. ACE enables ITF to test an entire network of unique capabilities at the same time without interrupting airport operations, and to assess the impact of innovative solutions on the ecosystem holistically, to ultimately inform requirements for future screening environments across TSA.
In partnership with McCarran International Airport as an ITF demonstration site, TSA can utilise a new checkpoint in Terminal 3 for assessment purposes as an ‘Innovation Checkpoint.’ This will showcase unique opportunities to modify and define the future aviation security process – beginning with ACE.
The ACE mission is to provide an environment that allows for the concurrent assessment of new technology and processes, enabling data-driven decision making.
ACE will accelerate learning, refine capabilities and gather requirements to better position TSA to make security decisions. ITF will share data with vendors to enable continuous refinement of their capabilities and share lessons learned to directly inform requirements generation for capabilities of interest to TSA.
ITF will also leverage the ACE checkpoint environment to assess strategies and process improvements to enhance the TSA officer experience.
Protecting the future
TSA is building a culture of innovation that anticipates and rapidly counters the changing threats across the transportation system. By establishing and promoting mechanisms to foster continuous improvement, TSA is positioned to best anticipate and counter the evolving threat to aviation.
Source:
https://www.internationalairportreview.com/article/101688/advancing-the-checkpoint-environment/