Security
You Can Now Block People from Adding you to Groups Thanks to this New Whatsapp Privacy Feature

Ever get tired of being added to different Whatsapp groups without your permission? Well Whatsapp is finally rolling out a solution for that problem.
Whatsapp announced on Wednesday the introduction of new privacy features that lets users limit who can add them to group chats.
One notable privacy feature is the introduction of an invite system that basically requires a user’s consent before they can be added to groups. Under this system, users will receive an invite link which carries basic information about the group. Users can choose to join the group via that link; otherwise the link expires in 24 hours.
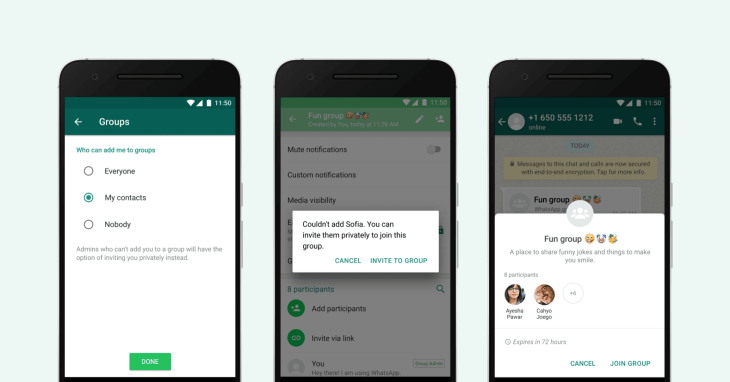
Even better, Whatsapp has introduced a feature that allows you to block anyone from being able to add you at all.
With the new privacy feature, you can select who can send you group invites.
Options available include “everyone”, “my contacts” or you can choose to block all invites totally using the “Nobody” option. These options are available under Account > Privacy > Groups in the Whatsapp settings.
Whatsapp announced that the new features are part of updates rolled out beginning on Wednesday. Full global rollout is expected to be completed over the next few weeks.View image on Twitter


Best News of The Day .
Now, You Can Choose To Join #WhatsApp Group .
The new feature lets you prevent people from adding you to their shitty groups. The feature will roll out soon for users in India.234:38 AM – Apr 4, 2019See Kumar Manish’s other TweetsTwitter Ads info and privacy
Whatsapp group is a highly functional and timely feature, but it’s also one of the most abused Whatsapp feature. Without seeking user permission, administrators of different Whatsapp groups annoyingly add users to groups.
Some users immediately choose to leave these groups. But some others may not feel like they can leave. For family groups and groups created by someone they know, users feel guilty leaving or hate it when their exit is announced by Whatsapp. As a result, more Whatsapp users prefer not even joining these groups in the first place.
Whatsapp Using New Groups Privacy Feature To Address Fake News
However beyond this, the latest group restriction plays well in the fight against fake news. In countries like Brazil and India, Whatsapp groups are important points to spread fake and misleading news.

Shashi Tharoor✔@ShashiTharoor · 14hReplying to @ShashiTharoor
It shows contempt for the voters to seek to exploit their ignorance of the source & context, which in any case was accurate about the past it describes. Unfortunately many are taken in by these lies. BJP is incapable of being ashamed of itself; but why can’t social media act?

I call on those who run @whatsApp, @Facebook & @Twitter in India&who claim to be concerned about the misuse of their platforms by political fake-news peddlers to make an example of this specimen, to start with. The echo-chamber repeating her lies is part of an organised campaign.1,8588:06 PM – Apr 3, 2019Twitter Ads info and privacy533 people are talking about this
Several reports show that in India, some political parties create groups based on caste, income levels and religion. With this classification, they bombard these groups with different reports designed to influence their thinking and conversations.
To address these issues, Whatsapp has already introduced several features. Some include labeling forwarded messages and limiting the number of times a message can be forwarded to five.
The new group invites system and blocking tools will help protect users even further.

