Security
Microsoft adds new ‘passwordless’ sign-in option with latest Windows 10 20H1 test build
Microsoft is continuing to roll out new Windows 10 20H1 test builds with incremental new features regularly. On July 10, the company delivered Windows 10 Build 18936 to 20H1 testers in the Fast Ring.
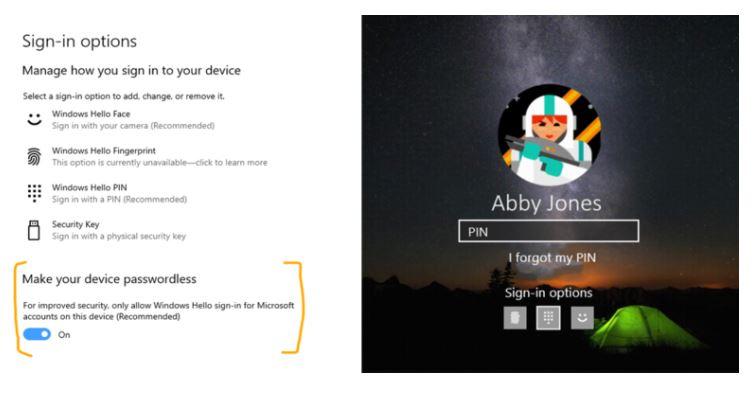
Today’s test build adds a new “Make your device passwordless” sign-in option in Settings. By going to Settings > Accounts > Sign-in options and turning on the passwordless option, users will switch all Microsoft accounts on that Windows 10 device to use Windows Hello Face, Fingerprint, or PIN only. As Microsoft notes in its post on today’s test build, this feature is rolling out to a “small portion” of Insiders and will go to more within a week.
Speaking of passwordless, Microsoft also made available today a public preview of FIDO2 security keys support in Azure Active Directory, which means users can try out the ability to deliver at scale FIDO2 security keys authenticating a user on a Windows 10 Azure Active Directory-joined device.
Today’s build also adds a new option to create a quick event from the Taskbar by clicking on the date in the taskbar. Users will see a calendar flyout so they can pick their desired date and set a time and location more quickly this way.
Microsoft also is expanding the availability of the phone screen feature in its Your Phone companion app to more PCs. This feature will be available on Surface Laptop and Laptop 2; Surface Pro 4, 5 and 6; Surface Book and Surface Book 2 starting with Build 18936.